
Connected Cars and Mobile Security
Changes are occurring in industrial control systems in factories and work-sites, in smarter appliances in our homes, in newer gadgets for health and fitness, and in highly assisted driving as well as autonomous vehicles on roads around the world. The benefits of the IoT may very well exceed the hype that surrounds it.
If we look back at computing systems history, just about any computing device which had been connected to a communications network has contained some form of vulnerability, experienced an attack, and required subsequent change to become more resilient, secure, and protected. In this era of Internet of Things we must be concerned and attentive to security issues and at the same time realize that every system has, or will have, a vulnerability at some point in time. Part of the solution for this inevitability is making sure that there are appropriate procedures, mechanisms, and attention paid to address issues that are discovered long after the devices are introduced into the market.
IoT devices, ranging from remote sensors and actuators to instrumented manufacturing facilities to connected vehicles must be treated as highly sophisticated computing systems that are now connected to a communications network. As such, the same core set of security characteristics must be applied to these devices as have been learned and applied to networked computing systems over the history of building and delivering computing systems. Authentication, Authorization, Auditing and Administration must all be considered. Confidentiality, Integrity, Availability, and Privacy of information must also be considered.
What is new in this era of the Connected Everything is that the devices which are being connected to communications networks are now much greater in number – by orders of magnitude, often-times constrained in their compute capacity, have sporadic or often-changing network connectivity, have battery power and/or heat limitations which reduce effective computing capacity, and are in control of physical elements which could pose a risk to human, environmental, or structural safety. We are in a situation of needing to apply known security techniques to a new environment which operates under a set of additional constraints. These techniques must also be applied to environments where existing equipment is outfitted with additional sensor and actuator technologies connected to communications networks through gateway computing devices.
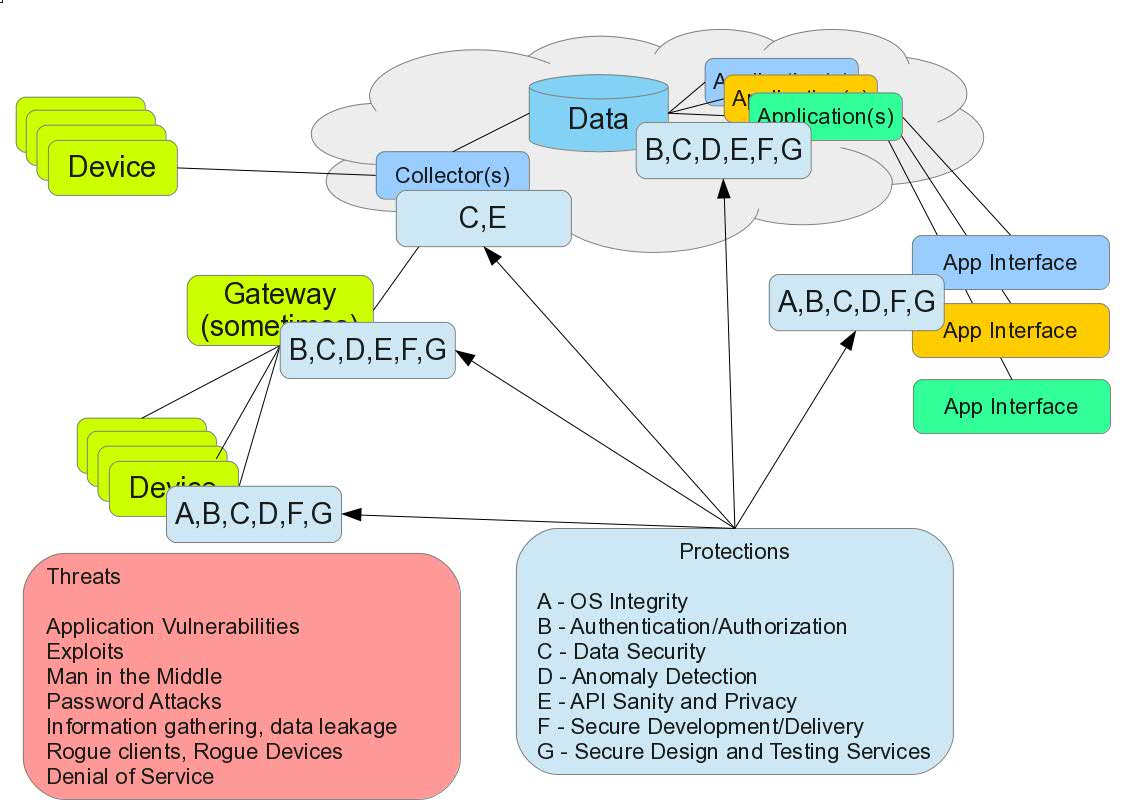
By applying a secure engineering methodology to the design, development, delivery, operations, management, and usage of these systems we can protect against identified threats and be prepared to detect, react, and recover from threats which are invented and discovered after the devices are introduced into the working environment. But what does this entail? Here is a brief list to get teams started:
- Establish a secure hardware/software development process which includes code management, automated build and automated testing, and streamlined packaging and software delivery mechanisms. Include source code analysis to identify vulnerabilities as well as security-related testing to identify runtime vulnerabilities. Software delivery also applies to device firmware/software updates as well. As more and more software is running in a wide range of distributed IoT devices, the need to update that software in a secure, timely, and cost-effective way also increases in importance. A secure, verifiable, and audited software/firmware update is part of a secure development and deployment process.
- Utilize authentication and authorization (access control checking) for devices, users, and applications which will interact with one another as part of the Internet of Things solution. Mobile security factors into this since many of the user interfaces for these IoT-related applications will be surfaced via mobile devices.
- Insert auditing/logging of both successful and unsuccessful requests for processing and utilize monitoring and alerting technology distributed across the set of computing systems. This implies that there should be some level of audit logging and monitoring in-vehicle, in-network, and in-mobile devices. Also necessary is detection of denial-of-service and distributed denial-of-service attacks against devices and the systems which support these devices.
- Secure all communications channels such that sensitive information is protected from observation, change, or corruption. Validate input and output parameters to ensure that inadvertent command invocation or escalation of privilege is not possible. Mobile security also applies to communications security since in some solutions mobile devices act as gateway systems to enable communications between connected devices and applications running remote from the devices.
- Design and implement defense-in-depth into the IoT solution. In some cases, this will require the insertion of gateway computing elements to serve as a layer of defense as well as a point at which isolation can be enabled to ensure safe operation in a disconnected, degraded, but still fail-safe mode. In other cases, this suggests inserting a layer of indirection or separation to allow for command and data checking, filtering, and logging.
- Be attentive to availability and safety. Above all else, the system must be engineered to do no harm as a result of its connected-ness and the control which may be possible to be exerted on the device by virtue of that connection. Fail-safe operation, dropping down in capability but being sure to bring the system to a safe steady-state, must be built into the connected device.
We are entering an amazing era of Internet of Things computing where cyber-physical systems are able to provide a more streamlined, comfortable, and even safer environment to work, play, and live. With this increased set of capabilities will come some risks and vulnerabilities to be addressed. By implementing IoT solutions using methods and technologies that we learned through years of experience, and having a strong means of responding to incidents and delivering updates, we can welcome this era with open arms and much excitement.
About the authors:
Chris Poulin is research strategist in IBM’s X-Force R&D team. He is responsible for analyzing security trends and emerging threats with focus on security for the Internet of Things.
Tim Hahn is an IBM Distinguished Engineer with IBM. As the Chief Architect for Internet of Things Security within the IBM Analytics organization, he is responsible for strategy, architecture, and design for IBM’s Internet of Things offerings. Tim also has experience with both connected vehicles and connected products.
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News



